184 million main passwords leaked! Keep away from these 2 risks
Again in mid-Might, a safety researcher introduced the invention of an unencrypted database containing 184 million passwords. Discovered hosted on an internet site, the entries included main companies like Google, Microsoft, Fb, and Apple. In addition they prolonged to financial institution and authorities companies.
The huge 47GB database is now offline, after being reported to the web site host. However its existence nonetheless alerts two risks that you just shouldn’t ignore. They’re the explanation this report has lingered within the information, throughout tech websites and mainstream shops alike.
First, this information was almost definitely stolen instantly from customers by infostealers, a form of malware. This sketchy software program can present up on a PC or cellphone in just a few alternative ways—and at present, it’s a much less mentioned technique of assault, regardless of its potential for deep injury to your day by day life.
Second, affected accounts stay weak to takeover or exploitation. The consequence might be an account lockout, delicate information leaked (e.g., tax particulars or confidential enterprise plans), or stolen money.
Right here’s find out how to defend your self.
Infostealers are malware you’ll be able to simply keep away from
Shutterstock.com / solarseven
An infostealer is software program that copies information saved on or typed into your PC, then sends all of it again to the attacker. That features passwords—hackers typically goal saved information out of your browser, like login credentials, cookies, crypto pockets particulars, and autofill information.
In case your system is compromised, you’ll be able to find yourself shedding banking particulars, residence and work addresses, tax data, and yep, the password to your e-mail account. The energy of your password received’t matter if it’s outright stolen.
How infostealers seem on a PC or cellphone
Malware doesn’t randomly seem in your gadgets—it’s important to obtain and set up such apps. And attackers are difficult with how they get you to take action. For instance:
- You obtain a browser extension or app that performs a standard activity—and it truly works as marketed. However within the background, it’s additionally stealing information from you.
- You click on on a pretend hyperlink for official software program. (This latest instance had an additional gnarly twist, the place the malware contaminated the graphics card itself to evade detection.)
- You resolve to journey the excessive seas and obtain pirated software program. It installs malware alongside the app you wished.
How one can keep away from infostealers
Just a few common practices will enable you evade an infostealer an infection. A part of it begins together with your habits round downloaded software program, and the opposite half is maintaining your safety software program updated.
- Select well-known software program vetted by reliable sources like safety consultants and main tech websites. Free open-source options typically exist for widespread paid apps, in case you’re on a funds. (And generally there are even distinctive free instruments.)
- Click on rigorously. When taking a look at search outcomes, confirm the URL matches an official or recognized website. If it’s off or in any other case appears sketchy, cease and begin over.
- Run antivirus scans usually. As of late, this needs to be an automated course of. It doesn’t harm to verify on occasion that your software program is ready to auto-download updates, although.
Increase your account safety, ASAP

In case your password ever turns into compromised, two-factor authentication will stand between you and an attacker. (Simply watch out to not by chance give away your 2FA codes, too.)
PCWorld
As to your account passwords, you received’t have the ability to inform in case you had been caught on this information leak. The most secure strategy is to imagine you can be affected, and take precautions.
Right here, the aim is to defend towards different folks utilizing your leaked credentials for ill-gain. These steps received’t all the time defend towards sure sorts of infostealer assaults. (Extra on that in a second.)
- Allow two-factor authentication (aka multi-factor authentication) in your accounts, particularly your most necessary ones. It acts as a second checkpoint that an attacker should clear in an effort to entry your account. Having simply your password received’t be sufficient.
- Begin utilizing passkeys. In contrast to passwords, this login technique can’t be stolen and shared by attackers. They’re additionally easier to make use of, with no memorization concerned.
- Change the passwords to your most delicate accounts. This course of is best in case you use a password supervisor, which can each generate a robust, distinctive password and put it aside for you.
Why don’t these protecting measures rise up towards infostealers? Due to how authentication at present works on the internet. After you efficiently log in to an internet site, your browser shops a cookie that maintains your sign-in state. These cookies could be copied by infostealer malware.
Relying on how an internet site handles authentication (on this case, how delicate its course of is to this sort of assault), an attacker could then have the ability to use that stolen authentication cookie on their very own PC to log into your account. Neither two-factor authentication nor passkeys can defend towards that.
So once more, watch out about what you put in in your PC.
A fast guidelines for what to do
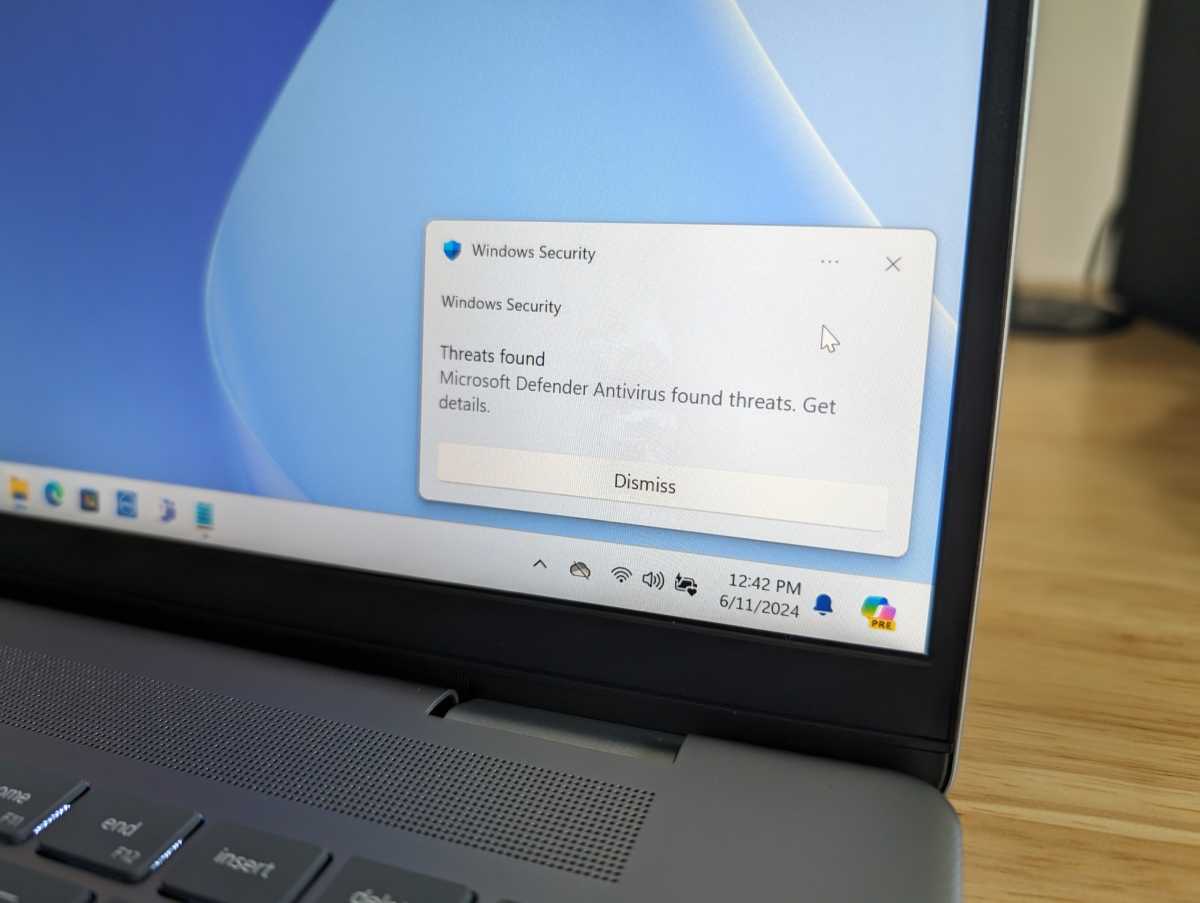
Chris Hoffman / IDG
Undecided find out how to deal with all these steps, and by which order? Mainly, be certain your PC is clear and freed from malware earlier than updating your safety data.
First:
- Run the antivirus software program in your PC.
- Additionally verify the apps and browser extensions put in in your system. (Antivirus isn’t idiot proof.)
- Take away any software program you don’t acknowledge or that has questionable origins. (You need to use a search engine to verify an app or extension’s popularity, in case you’re uncertain.)
Then:
- Allow two-factor authentication in your accounts with passwords.
- Replace your passwords for delicate accounts—main e-mail deal with and monetary establishments at minimal.
- Additionally think about making a passkey to your account, to make use of as your normal technique of login*.
You’ll be able to go totally passwordless for some accounts—that’s, swap over to passkeys and take away your password. This technique does run some danger of changing into by chance locked out of your account, although. You’ll need further passkeys saved on backup gadgets to forestall such a scenario.
My recommendation to most individuals: Improve your password to one thing random and really robust, then put it aside to a password supervisor. Additionally allow 2FA. Afterward, additionally create a passkey + a backup. Use the passkeys as your normal technique of login, however preserve the password + 2FA combo as a failsafe in case you lose entry to all of your passkeys.
Yeah, on-line safety is a significant ache proper now. (The explosion of AI instruments and their use by cybercriminals is a giant issue.) Hopefully, we’ll discover our strategy to a greater answer quickly.




