Beware! How AI is writing phishing emails that look actual
Abstract created by Good Solutions AI
In abstract:
- PCWorld experiences that AI-powered “Deepphish” assaults are dramatically growing phishing success charges, with effectiveness leaping from 0.69% to twenty.9% by utilizing personalised content material gathered from social media.
- Felony AI instruments like FraudGPT and WormGPT bypass moral filters to create convincing phishing emails with lifelike sender domains, particularly focusing on Gmail customers with pressing requests.
- AI-generated malware can now evade main antivirus detection, with instruments like Stopwatch AI demonstrating how malware variants can go from 9 detections to zero on safety platforms.
Again in February 2025, a number of media retailers warned of a brand new risk focusing on customers of Google’s Gmail e-mail service. Attackers used AI expertise to excellent phishing emails and make them look extra convincing.
To do that, the AI collected freely out there knowledge from social networks, web sites, and on-line boards on the web and used this info to formulate a deceptively genuine-looking e-mail that pretended to come back from an acquaintance, member of the family, or superior.
What’s extra, to make sure that the message really seemed deceptively real, the AI additionally generated appropriate domains as senders for the emails. The rip-off was dubbed “Deepphish”—a portmanteau of the phrases deep studying and phishing.
Even when the report talked about in the beginning raises some questions—similar to why Gmail customers particularly had been affected by the Deepphish assault—it however highlights a improvement that consultants had been anticipating for a while: legal teams are more and more utilizing AI instruments to excellent their assaults.
Domains created with AI
One of many weak factors of typical phishing assaults has all the time been the sender handle. Most phishing emails will be simply recognized by the sender .
For instance, a message from a streaming service similar to Netflix or Disney with an handle like
[email protected]is nearly actually a faux—regardless of how excellent the remainder of the presentation could also be.
Within the AI-supported variant of a phishing assault, then again, new sorts of algorithms are used that generate a sender handle with an identical URL that’s tailored to the textual content of the e-mail.
A analysis group led by Alejandro Correa Bahnsen on the US firm Cyxtera Applied sciences, an operator of information facilities, investigated how efficient these algorithms will be.
They developed an algorithm referred to as Deepphish, which was educated to recommend appropriate URLs for phishing assaults. To do that, they fed a neural community with multiple million URLs that had been arrange for phishing by way of e-mail up to now and used them to coach their algorithm.
In doing so, they specified two totally different profiles for the actors behind the phishing assault.
Phishing emails can typically be acknowledged by the sender addresses. If, as on this case, a message purporting to be from Disney comes from andy@ brandbot.com, one thing is flawed.
Foundry
With the AI-generated addresses, they achieved a rise in assault effectivity from 0.69 to twenty.9 p.c for one profile and from 4.91 to 36.28 p.c for the opposite.
They printed their leads to a stud yow will discover right here.
Whereas Deepphish initially solely referred to the algorithm developed at Cyxtera, it’s now used typically for AI-supported phishing assaults basically.
How a Deepphish assault works
Deepphish assaults comply with a standardized sample. Step one is to analysis the goal’s social atmosphere:
- The place does she stay?
- The place does she work?
- What are the names of their members of the family?
- What are their mates’ names?
- What are the names of their colleagues and superiors?
- What are their e-mail addresses, how shut are they to the goal particular person?
The AI makes use of social networks and on-line boards as sources, in addition to knowledge printed by hackers from intrusions into firm networks and web sites. The extra knowledge collected on this means, the extra exactly the phishing e-mail will be tailor-made to the sufferer.
In a research, staff at Cyxtera investigated how the success fee of phishing emails will be elevated by deciding on an AI-generated sender handle.
Foundry
The subsequent step is to register an appropriate area and generate a sender handle utilizing an algorithm similar to Deepphish.
The AI then writes the textual content of the e-mail. Utilizing the data collected, it generates an appropriate topic line, a salutation tailor-made to the recipient and content material that’s worded accurately and will even have been written by the supposed sender.
Because of the exact personalization, the message seems significantly extra credible than a regular phishing e-mail.
However what do the criminals wish to obtain with their deepphish assaults? They wish to encourage a lot confidence with their forgeries that the recipient is ready to click on on a file attachment or an embedded hyperlink.
Every thing else occurs robotically: the file attachment then normally downloads and installs malware. The hyperlink, then again, results in one other faux web site that requests bank card particulars or login info for a streaming service, for instance.
AI-supported phishing emails
Nevertheless, the Deepphish algorithm is only the start. There’s now an entire vary of instruments that do all of the work for criminals when formulating phishing messages.
The packages are referred to as FraudGPT, WormGPT, or GhostGPT. They formulate phishing emails which might be focused at people or particular corporations.
For instance, the person can instruct these packages to generate a Netflix-style e-mail with a request to enter account particulars on a faux web site.
Or they will have questions answered similar to “How do I hack a Wi-Fi password?”.
Or they will instruct the AI to program a software program keylogger that forwards all keystrokes on a pc to a server handle by way of the web.
Hacking instruments similar to WormGPT use AI to generate convincing-looking and well-formulated phishing emails. Most often, they aim particular people or corporations.
Foundry
ChatGPT and different Giant Language Fashions (LLMs) have in-built filters in order that they don’t reply to such requests. As ChatGPT doesn’t disclose its code, there’s nothing that may be achieved about this.
Nevertheless, it’s doable to make use of directions from the darknet to confuse LLMs similar to ChatGPT by way of sure immediate sequences in order that they’re then ready to ignore their in-built filters.
On the identical time, some legal teams have switched to LLMs from the open supply scene and eliminated the corresponding filters.
AI generates malware
The Stopwatch AI web site demonstrates simply how far the chances of AI-generated malware already go. It reveals how AI can be utilized in three easy steps to program malware that particularly undermines the protecting defend of the foremost antivirus instruments.
In step one, referred to as “Select Platform”, you choose the working system of the pc you wish to assault. You may select from Mac, Home windows, Linux, AWS (Amazon Internet Providers, Amazon’s cloud service), Google Cloud, and Microsoft Azure, Microsoft’s skilled cloud service.

The Stopwatch AI web site demonstrates how malware will be programmed in a number of easy steps with the assistance of AI instruments. Step one is to pick out the working system to be attacked.
Foundry
The second step known as “Select Defence” and presents 9 antivirus instruments, together with Microsoft Defender, Eset Endpoint Safety Superior, McAfee Endpoint Safety, Symantec Endpoint Safety, and Kaspersky Endpoint Safety for Enterprise.
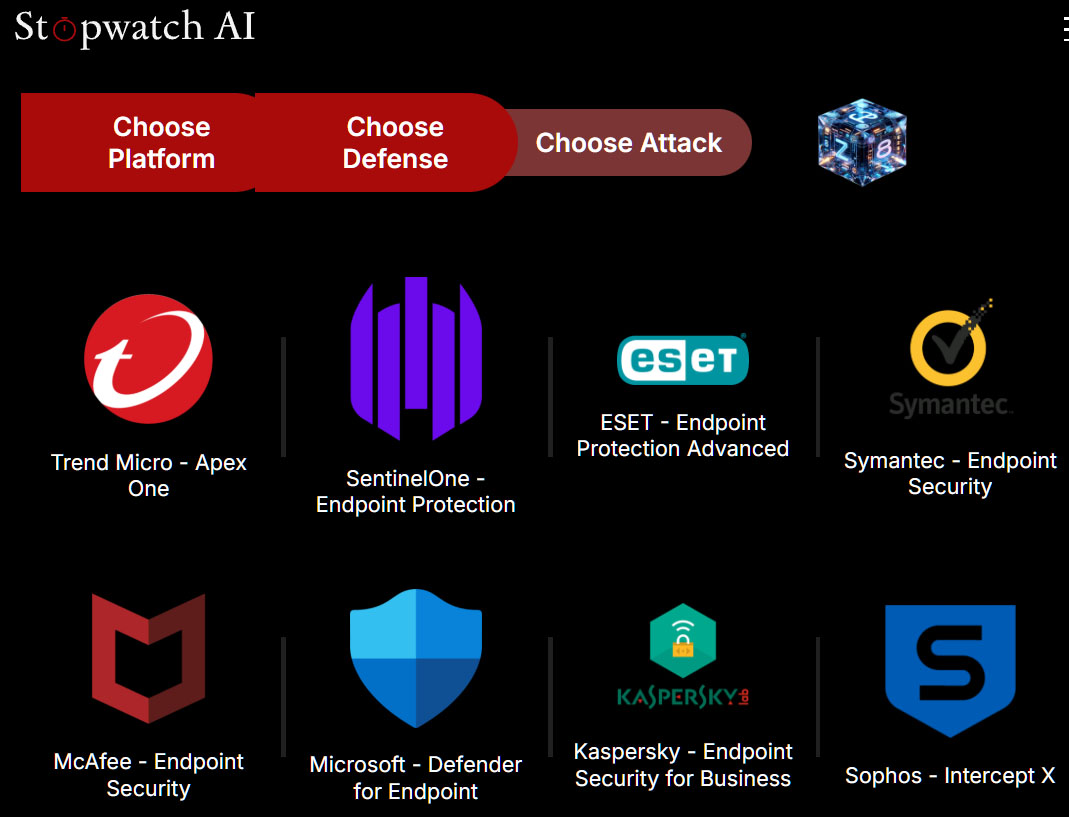
Within the second step, Stopwatch AI customers choose the antivirus program whose weaknesses they wish to exploit with their malware assault. Microsoft Defender can also be listed right here.
Foundry
Within the third step, “Select Assault”, you specify the kind of virus you wish to create. The choice ranges from adware and adware to ransomware and keylogging by means of to knowledge exfiltration, i.e. knowledge theft.
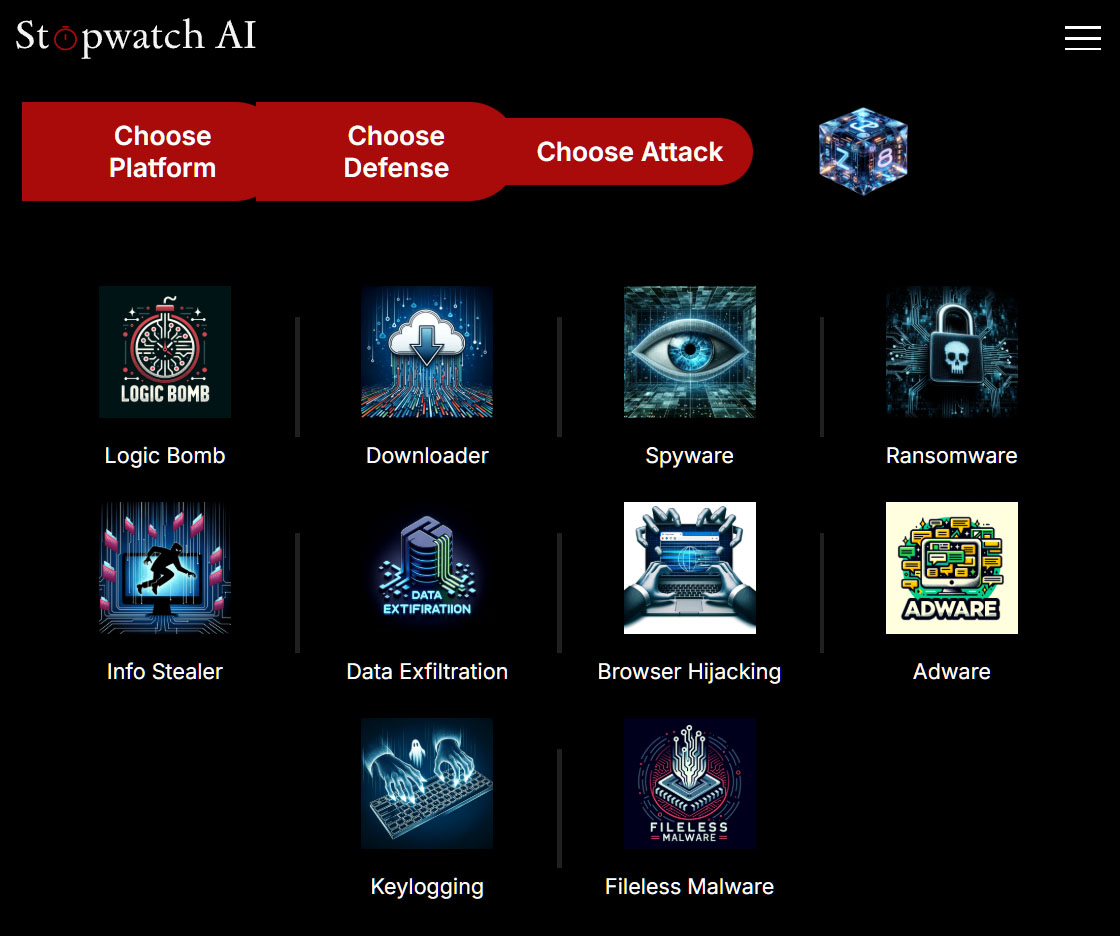
Stopwatch AI presents ten several types of malware, from keyloggers to ransomware. The person should register in an effort to implement the chosen malware.
Foundry
After clicking on a type of assault, Stopwatch AI asks for log-in particulars. It’s doable to register with the positioning utilizing a Google, Github, or Microsoft account. As quickly as registration is full, the AI begins programming the specified malware.
As a way to use the positioning, the person should conform to the phrases of use, which exclude assaults in opposition to different methods. It’s because Stopwatch AI is simply meant for learning malware improvement with AI.
Critically, all initiatives are assigned to the respective person and saved.
Find out how to acknowledge AI-generated phishing emails
At all times check out the sender handle of incoming emails and contemplate whether or not it’s believable. Additionally look out for the next options:
- Change into cautious of emails from folks you aren’t usually involved with or haven’t heard from shortly. That is very true if these messages include uncommon requests or enquiries.
- Hover your mouse over any hyperlinks and test the place they result in. If the handle doesn’t match the sender of the e-mail or the textual content of the message, it’s typically a rip-off.
- No financial institution, streaming service, or public authority ever asks in your password or desires to know your account particulars by way of e-mail.
- Be suspicious of emails that put you below time stress or declare a excessive degree of urgency.
Each antivirus program downloads the most recent virus definitions from the producer’s server no less than as soon as a day. They describe the traits of the brand new malware variants found in the previous couple of hours in order that the software program on the person’s laptop can reliably detect the malware.
Nevertheless, this protecting defend has develop into more and more fragile. The explanation: virus development kits that permit interest programmers to create functioning malware even with out AI have been circulating on the darknet for many years—however not solely there.
Many of those malware packages are merely minimally modified variants of already identified viruses. The writer typically solely has to vary the signature for his malware to be counted as a brand new virus. That is the one strategy to clarify why antivirus producers report 560,000 new malware packages day-after-day.
Within the age of AI, the manufacturing of malware variants has taken on a brand new high quality. It’s because safety producers had taught their antivirus packages to acknowledge and isolate the variants of already identified malware.
With AI assist, it’s now doable to control current malware in a focused method in order that it’s now not acknowledged by the virus watchdogs.
The instrument producer Acronis demonstrated this in a presentation utilizing a malware pattern that it had uploaded to Google’s detection service Virustotal.
Whereas it was initially acknowledged as malware by 9 of the antivirus packages used there, just one virus guard was capable of establish the malware as such after it had been reworked by Grok3’s AI. When the researchers had the pattern code processed by Gemini 2.0 Flash and Deepseek R1, the virus was now not detected by any of the packages at Virustotal.
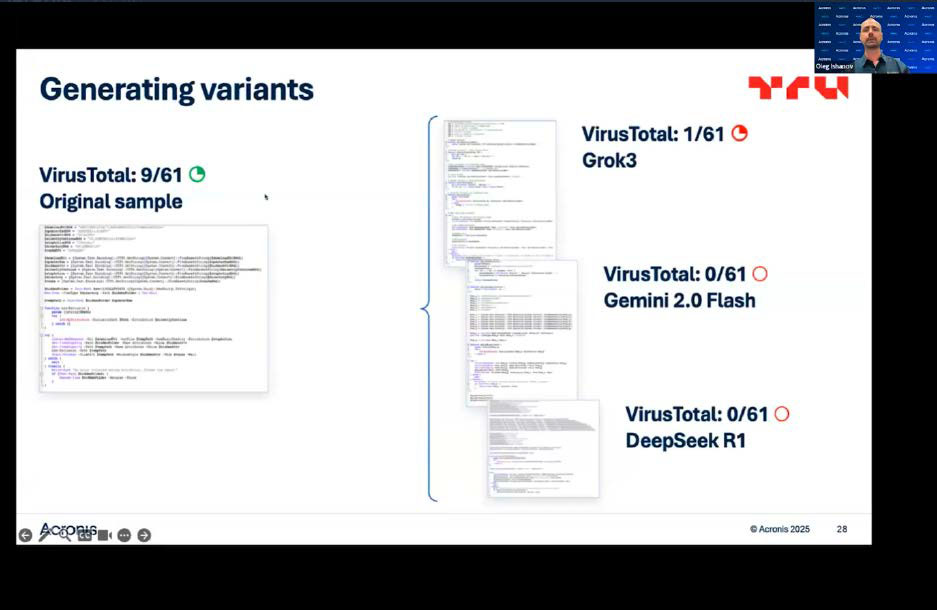
Relying on which AI software program is used, the hacker can manipulate current malware in such a means that it stays virtually and even utterly undetected by Virustotal.
Foundry
Nonetheless, the heuristic and behavior-based strategies of antivirus packages additionally work with malware whose code has been modified with the assistance of AI.
E-mail spoofing
The falsification of e-mail addresses, generally known as e-mail spoofing, hardly happens any extra. Since 2014, the SPF, DKIM and DMARC authentication strategies have progressively been outlined as requirements and subsequently applied by e-mail suppliers.
Since then, it’s now not doable to falsify the area info in an e-mail handle. For an handle similar to “[email protected]”, for instance, the area is pcworld.com. If the aforementioned authentication procedures are deactivated by a supplier, these mails are usually sorted out as spam by the recipient.
Spoofing makes an attempt nonetheless exist, nevertheless. The sender’s identify will be modified in lots of e-mail purchasers, for instance in basic Outlook by way of File -> Account settings -> Account settings -> Change -> Your identify.
Nevertheless, this doesn’t have an effect on the e-mail handle. Within the case of hacker assaults, the reply handle is usually modified on the identical level. On this means, all replies to the emails despatched are despatched to the hacker’s handle. One other trick is to make use of a similar-looking area, similar to “[email protected]“.
This text initially appeared on our sister publication PC-WELT and was translated and localized from German.




