4 adjustments I made instantly after 1.3 billion passwords had been stolen
Earlier this month, safety guru Troy Hunt added a staggering two billion distinctive e-mail addresses and 1.3 billion distinctive passwords to his Have I Been Pwned and Pwned Passwords databases. Aggregated by Synthient, the info comes from a number of credential stuffing sources shared by menace actors, in addition to knowledge stolen immediately from people by infostealer malware.
The variety of folks affected is so huge that the rollout of notifications went out in waves to Have I Been Pwned subscribers. (This service is free—enter your e-mail handle into the HIBP search area, after which click on on the Notify Me button that seems earlier than any outcomes.)
The information additionally has specific traits that stood out to me. (You possibly can learn extra about them in Hunt’s weblog put up.)
Between these particulars and the questions I’ve fielded about what to do subsequent, I’ve modified my recommendation on the “proper” strikes for good on-line safety.
Right here’s what I now advocate.
Totally different e-mail addresses for each account
Utilizing the identical e-mail handle to log into every of your accounts makes a hacker’s job simpler. They’ll plug that information into an internet site together with any password they suppose (or know) you’ve used.
This credential stuffing assault usually works as a result of folks reuse passwords. So a straightforward solution to keep away from getting tripped up this manner: Use a special e-mail handle for each account.
Within the outdated days, you needed to create an precise separate account every time you wanted a brand new e-mail handle. Not anymore.
You possibly can create and handle masked emails for all of your on-line accounts so distributors don’t see your precise e-mail handle.
Michael Ansaldo/Foundry
These days, you should use e-mail aliases (aka “e-mail masks” or “masked e-mail”) for a similar objective. To different folks, it is going to look like you might have a special e-mail handle throughout your accounts. In the meantime, you’ll be able to obtain messages multi function place (should you so select). An alias forwards your emails wherever you need them to go.
Essentially the most fundamental model of an e-mail alias is the power so as to add further textual content to the tip of your e-mail deal with (e.g., [email protected]). The format is the plus signal (+) after which no matter string of letters and numbers you wish to add. Gmail and Proton Mail are two e-mail companies that assist this type of e-mail alias.
For added privateness, you should use devoted e-mail masks to fully cover your true e-mail handle. For instance, you obtain e-mail at [email protected], however you’d want it to maintain that information non-public. So you utilize the built-in masked e-mail characteristic supplied by your e-mail service (if relevant) otherwise you join an unbiased service to generate random e-mail aliases like [email protected] or [email protected].
PCWorld
Proton Mail, Fastmail, and Apple’s iCloud Mail are all examples of e-mail companies that embrace e-mail masks. (Proton Mail and iCloud Mail name them “hide-my-email” aliases.) You can even join Mozilla Relay, SimpleLogin, or one other e-mail masking service if you have already got an e-mail handle elsewhere that you just’d fairly hold utilizing.
A fundamental alias that depends on a +extratext type addition to your e-mail handle helps to at the least hold every login more durable to guess. (Add textual content to your e-mail handle that isn’t apparent or guessable based mostly on the web site information. For instance, keep away from +goal should you’re on Goal.com.)
However having each safety and privateness is the higher name today—it makes it more durable for somebody to construct a profile of you to create customized, more practical phishing emails and textual content messages. So a really nameless e-mail alias service is the higher solution to go.
Replace your outdated passwords
In Troy Hunt’s writeup about importing the password knowledge, a couple of one who responded to his inquiry estimated the age of their compromised passwords falling between 10 to twenty years outdated.
Amongst a few the hinted traits of those historic credentials: They weren’t lengthy, for starters—about eight characters. And so they included variations that hardly counted as such. (One particular person confirmed {that a} compromised password solely tacked on two further exclamation marks (oof) to the tip of one other compromised password.)

Hive Techniques
What makes for an excellent password has modified so much prior to now decade, and particularly so prior to now 20 years. If in case you have outdated ones you might have by no means up to date, it’s time to revisit them. Shorter passwords are straightforward to crack now, because of enhancements in computational efficiency. And what we thought of random and robust in 2005 (e.g., p@$$phrase!) isn’t in any respect now.
Plus, with web site breaches occurring left and proper as of late, you can have a fairly decently random password with the magic mixture of 1 lowercase, one uppercase, a quantity, and a particular character—but it surely may nonetheless be compromised since you’ve used solely weak variations of it. (Or worse, have been outright reusing it.)
Even should you’re not utilizing outdated accounts anymore, don’t depart them weakly protected with a crappy password. You’ll have different data like addresses, cellphone numbers, and different knowledge that may be stolen and used for focused phishing assaults.
Clear up (or delete) outdated accounts
Talking of stealable private data—when you’ve got accounts you utilize sometimes, filter particulars that don’t want to remain on file. Even when your password’s by no means stolen, the info may nonetheless leak if the web site proprietor is a sufferer of hackers.

Jared Newman / Foundry
Bank card information is the very first thing I delete on purchasing accounts. (Higher to avoid wasting that in your password supervisor, if you’d like the comfort of autofill.) However you’ll be able to wipe your own home handle, cellphone quantity, and different particulars, too, to make it more durable for a hacker to determine your habits and guess on the smartest solution to trick you out of your cash (or invaluable information that will cause them to your cash).
Not planning to ever use the account once more? Or so sometimes that it wouldn’t matter should you pay in your gadgets as a visitor? Simply delete the entire thing.
Change to passkeys
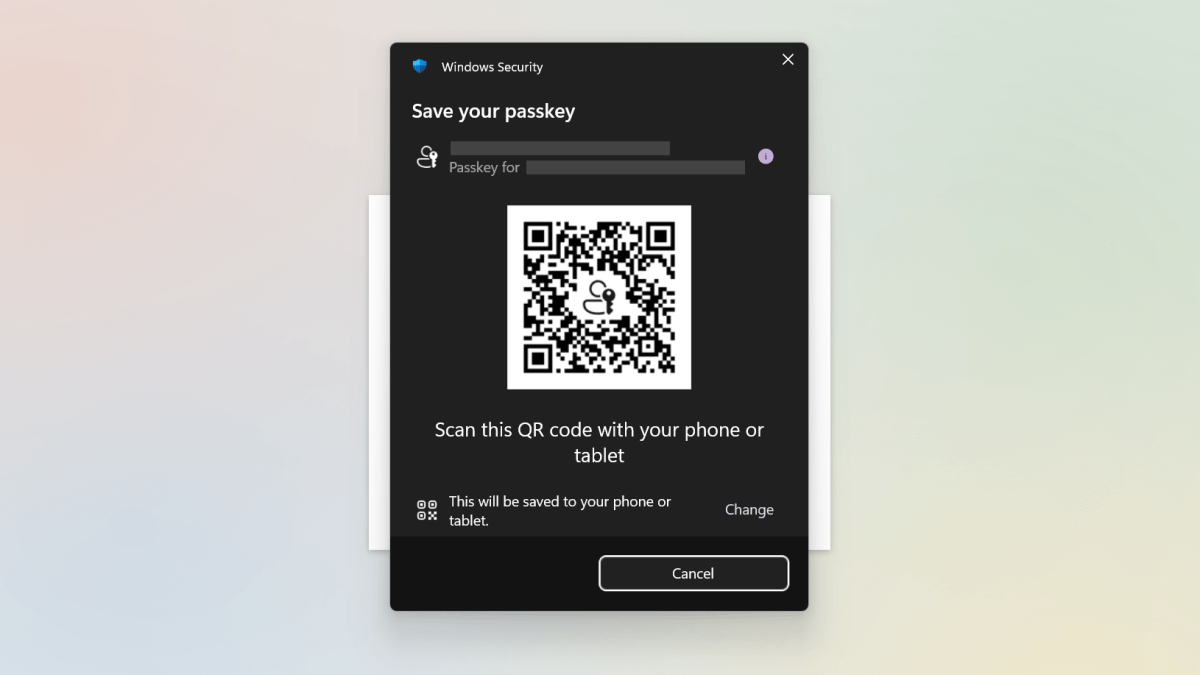
I beat this drum arduous today, and for good cause. A hacker can discover out your e-mail handle and your outdated passwords, certain. However should you swap your major login technique to a passkey, that gained’t do them any good.
Passkeys work in a different way than passwords. They’ll’t be stolen immediately or used remotely by unauthorized units. (A hacker may break into the account the place you retailer passkeys, should you hold them in a cloud-based service, however that’s totally different.) They’re additionally tied to the web site they had been created for.
PCWorld
So a credential stuffing assault gained’t work on a passkey-guarded account. And should you ever by chance fall for a phishing hyperlink, it gained’t work on the phony website.
Some web sites don’t permit passkey-only login, so for these, replace your password to one thing lengthy, distinctive, and random after which reserve it in your password supervisor as a backup technique for log in. (Allow two-factor authentication, too.)
However in any other case, passkeys are the best way to go. You don’t have to consider them as soon as they’re arrange. They only work.




