Microsoft fixes dozens of safety flaws in Home windows, Workplace, and Azure
Abstract created by Sensible Solutions AI
In abstract:
- Microsoft launched safety patches for 31 vulnerabilities throughout Home windows, Workplace, and Azure, together with two actively exploited zero-day flaws.
- PCWorld reviews that CVE-2026-21514 impacts Microsoft Phrase, permitting code injection via malicious recordsdata, whereas CVE-2026-21510 bypasses Home windows SmartScreen safety.
- Crucial vulnerabilities additionally influence Desktop Window Supervisor, Distant Desktop Service, and Web Explorer’s legacy capabilities, requiring rapid patching.
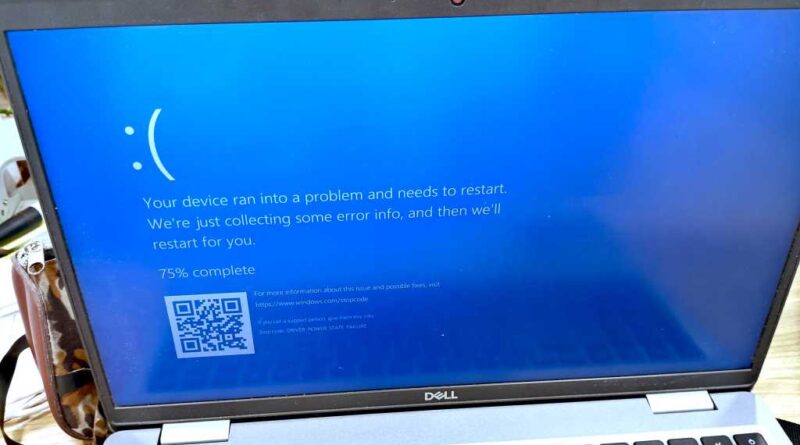
Yesterday, February tenth, was Patch Tuesday. Microsoft launched safety updates to handle 58 new safety vulnerabilities.
Along with Home windows and Workplace, Alternate Server, Web Explorer, Azure, and the Home windows Subsystem for Linux (WSL) are additionally affected. Six zero-day vulnerabilities are already being exploited within the wild, and 5 vulnerabilities are categorised as essential.
The subsequent Patch Tuesday is predicted on March tenth, 2026.
Microsoft Home windows updates
Numerous the fastened safety vulnerabilities—31 this time—are unfold throughout the varied Home windows variations (10, 11, Server) for which Microsoft nonetheless affords safety updates. Home windows 10 continues to be listed as an affected system, though help formally expired in October.
Two Home windows zero-day vulnerabilities had been already publicly recognized and are being exploited within the wild. Each are SFB (Safety Characteristic Bypass) vulnerabilities. The CVE-2026-21510 vulnerability within the Home windows Shell permits an attacker to bypass SmartScreen and Shell safety checks with the intention to execute arbitrary code. A person merely has to open a shortcut for the malicious code to be executed.
Anybody who thought they had been lastly rid of the previous browser zombie Web Explorer (IE) is mistaken. It’s nonetheless current in all variations of Home windows, as many applications nonetheless depend on sure IE capabilities. These legacy points are lowering over time, however nonetheless exist. Attackers can exploit SFB vulnerability CVE-2026-21513 to bypass safety checks and achieve unauthorized entry.
The CVE-2026-21519 vulnerability in Desktop Window Supervisor (DWM) is already the second DWM vulnerability this yr to be exploited. Attackers can achieve elevated privileges and execute code with system permissions. To do that, they mix the DMW vulnerability with an RCE vulnerability, of which there are lots.
CVE-2026-21533 is one other EoP (Elevation of Privilege) vulnerability. It’s discovered within the Distant Desktop Service. Opposite to what the affected Home windows part may counsel, this bug is exploited regionally to achieve elevated privileges. As with the DWM vulnerability, if profitable, an attacker can execute code with system privileges. Computer systems working the susceptible Distant Desktop Service may be an attention-grabbing intermediate goal for lateral motion after penetrating a community.
The final zero-day vulnerability on this sequence is CVE-2026-21525, a DoS vulnerability within the Distant Entry Connection Supervisor. An attacker might crash the service. Because it’s unclear whether or not it’s going to restart mechanically, the attacker might probably preserve an administrator who desires to intervene remotely at bay. In any other case, DoS vulnerabilities are not often utilized in extra complicated assault situations.
Microsoft Workplace updates
Microsoft has fastened six vulnerabilities in its Workplace household, all of that are categorised as excessive danger. At first look, these don’t embrace any RCE (Distant Code Execution) vulnerabilities.
Nonetheless, the Phrase vulnerability CVE-2026-21514, categorised as a zero-day and SFB (Safety Characteristic Bypass) vulnerability, can be used to inject and execute code. A minimum of the preview window isn’t an assault vector right here—a person should open a ready Workplace file utilizing Phrase to allow a profitable assault by way of this vulnerability.
Microsoft Azure updates
February’s Patch Tuesday doesn’t embrace any safety vulnerabilities categorised as essential with regards to desktop computer systems or servers on native networks, however there are 5 safety vulnerabilities recognized as essential that have an effect on Microsoft’s Azure cloud platform.
Microsoft has already fastened three of them and is within the strategy of documenting them. Two vulnerabilities have an effect on confidential ACI containers (Azure Container Cases) and require motion to safe them.
Microsoft Edge updates
The newest safety replace to Edge 144.0.3719.115 dates from February fifth and is predicated on Chromium 144.0.7559.133. It fixes two Chromium vulnerabilities. Nonetheless, Google has since launched Chrome and Chromium 145. A corresponding Edge replace is predicted to be launched on the finish of this week.
Microsoft has additionally closed a spoofing vulnerability (CVE-2026-0391) in Edge 143 for Android. This was already finished again in December, however is barely now being publicly documented.
This text initially appeared on our sister publication PC-WELT and was translated and localized from German.