Ransomware: What the LockBit 3.0 knowledge leak reveals
On 7 Might 2024, the presumed id of the operator of the LockBit 3.0 franchise, also referred to as LockBitSupp, was revealed throughout UK Nationwide Crime Company and its companions’ Operation Cronos: Dmitry Yuryevich Khoroshev.
One yr later, to the day, the whole contents of the SQL database of an online administration interface for the corporate’s associates was made public. And never simply wherever – on the ransomware franchise’s web sites. The irony is – they had been hacked. The info was extracted on 29 April. It considerations a system that was arrange on 18 December final yr.
A uncommon mild
This knowledge offers unprecedented visibility into the actions of the LockBit 3.0 ransomware. The compilation dates of the encryption malware make it attainable to regulate earlier estimates of assault incidence dates. Within the case of sure recognized victims, they’ve already revealed a spot of as much as 10 days between the top of the exfiltration of the sufferer’s knowledge and the launch of the encryption. This underlines the significance of efforts to detect such exfiltration.
This knowledge may also be used to attribute totally different victims to their attackers. This grouping shall be helpful for analysing negotiation strategies and monitoring any ransom funds.
LeMagIT
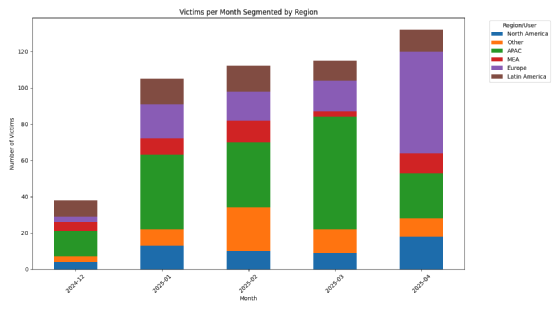
This administration interface for associates contained 75 person accounts, two of which had been most certainly utilized by LockBitSupp itself. At least 35 accounts had been “paused,” two of which had been used in opposition to victims in Russia. The firm’s operator has assured that that is the rationale for his or her suspension.
However solely 44 accounts had been really used to generate ransomware and probably launch cyber assaults. Of those, 30 had been energetic on 29 April, however solely seven seem to have been engaged in conducting assaults at the moment.
LeMagIT
A geographical unfold
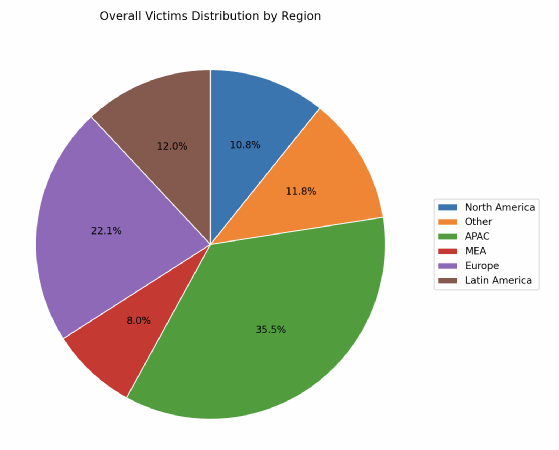
Analysis into the geographical origins of the victims talked about reveals an uncommon pattern – in all probability, the Asia-Pacific area was the main focus for 35.5% of the efforts of LockBit’s associates over the interval in query, in contrast with 22% for Europe, and fewer than 11% for North America, behind Latin America at 12%.
LeMagIT
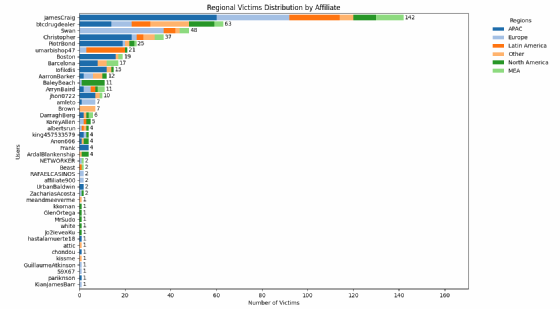
However there are very marked disparities between associates. PiotrBond, for instance, targeting the Asia-Pacific area, with 76% of its victims. The identical applies to Umarbishop47 (81%). DarraghBerg wager equally (33.3%) on this area and Africa-Center East. However JamesCraig additionally gave precedence to Asia-Pacific (42%).
This geographical evaluation additionally highlights the dearth of observability of the risk on this area, notably in China, which accounted for 51 victims within the pattern studied. Indonesia comes an in depth second with 49 victims, adopted by India (35).
LeMagIT
The info additionally means that South Korea is globally under-represented in observable malicious exercise.
This uncommon geographical distribution might mirror adjustments within the profiles recruited by LockBit 3.0. Essentially the most energetic associates don’t appear to be those that go after probably the most engaging victims.
The reflection of a tarnished picture
The obtainable knowledge suggests as a substitute that those that multiply their victims attempt to goal doubtlessly much less mature folks than others, even when they should pay modest sums, in international locations with per-capita incomes world wide common.
The negotiations noticed help this evaluation, with ransom quantities very continuously requested of lower than $20,000.
All in all, the LockBit 3.0 banner at present seems to have solely two or three energetic high-flying associates. That is solely half a shock – the Cronos worldwide judicial operation dented the picture of the mafia-like franchise. If it manages to draw anybody, its enchantment is, unsurprisingly, restricted.
It even makes you wonder if some victims who refuse to pay the ransom are intentionally not being claimed on LockBit’s showcase web site in order to not tarnish its picture even additional.
And this new leak is unlikely to enhance issues – it has uncovered the Tox encrypted e mail IDs of sure associates, their passwords (saved in clear textual content), and pseudonyms with which sure open supply intelligence specialists will little question be comfortable to analyze – to not point out the victims’ personal encryption keys.




